
The Christmas Tree Packets
As we're entering Christmas season, it's time to focus on what really matters: Christmas Tree Packets and Christmas Tree Attacks.
Let's get technical...
A TCP IP packet contains not only the data you want to send over the network, but also additional information so that IP devices can route the packet to its correct destination, like a tag on your packet. This information is contained in the packet header:
Let's quickly describe each part:
- Version: IP version of the packet.
- IHL: Length of the header (Internet Header Length).
- Service type: Desired quality of service.
- Total Length: Length of the packet, including header and data.
- Identification: Unique fragment identification.
- Flag: Sets various control flags.
- Fragment Offset: Indicates where this specific fragment belongs.
- Time to Live (TTL): Value between 1 and 255, decreases each time the packet is forwarded, and the packed is dropped if the value reaches 0. This mechanism keeps undeliverable packets from traveling for an indefinite amount of time.
- Protocol: Upper-layer protocol used in the data portion of the packet.
- Header Checksum: Header error detection mechanism.
- Source address: IPv4 address of the sending endpoint (32-bit binary value).
- Destination address: IPv4 address of the receiving endpoint (32-bit binary value).
- Options: Optional parameters.
- Padding: Used to make sure the header ends on a 32-bit boundary.
There's a lot to describe, but what interests us here is the "flag" area.
The flag area contains 9 bits:
- Nonce Sum (NS): Enables the receiver to demonstrate to the sender that segments are being acknowledged.
- Congestion Window Reduced (CWR): Acknowledge that the congestion-indication echoing was received
- Explicit Congestion Notification Echo (ECE): Indication of congestion.
- Urgent (URG): This data should be prioritized over other data.
- Acknowledgment (ACK): Used for acknowledgment.
- Push (PSH): Indicates that application data should be transmitted immediately and not wait for the entire TCP segment..
- Reset (RST): Indicates that the connection should be reset.
- Synchronize (SYN): Synchronize sequence numbers.
- Finish (FIN): Indicates there is no more data from sender.
A Christmas Tree Packet can be created by setting the URG, PSH, and FIN flags of the TCP header.
This is how the flag area of such a packet will be displayed in Wireshark:
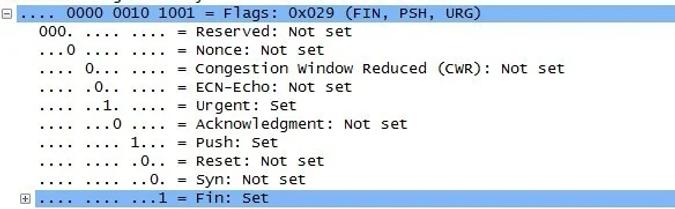
And this is where the Christmas tree appears... If you can't see it, look at the position of the 1s in the following picture:
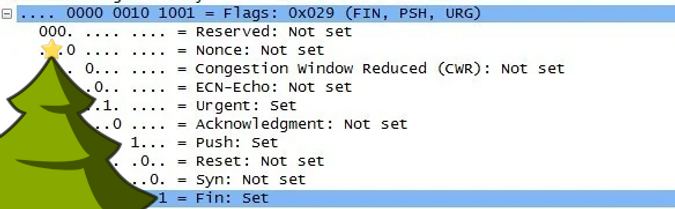
What does a Christmas Packet do?
Well, first of all, a Christmas Packet exploits a loophole with the TCP RFC 793 to differentiate between open and closed ports.
"According to RFC 793, if a closed port gets a TCP packet without the SYN, RST, or ACK flag being set, it is suppose to respond with a RST packet. If the port is open, the TCP stack is suppose to just drop the packet without giving a response. Not all Operating Systems follow the RFC to the letter however, and these discrepancies allow for OS fingerprinting"
So a packet crafted this way can be used for reconnaissance, easily bypassing filters and firewalls. And some operating systems might even send an RST response with a listening socket instead of dropping it.
Christmas scans (or Xmas scans) will often be created by sending random TCP ports in an array of packets, each with a different TCP destination port. Sometimes, even the source port is randomized.
How harmful is that?
Being able to launch a reconnaissance attack on your network is already a serious security concern, and this is mainly due to what is "not defined" in the packet, but what "is" defined is no less problematic.
After all, every child who receives a Christmas present will stop their activity until the package is opened...
By setting up the URG, PSH, and FIN flags of the packet header, the attacker ensures that any network device will proritize processing this packet over anything else, and most of the times this type of packet will require more processing power than a typical one. The result is that sending a large number of Christmas Tree Packets can lead to a Denial-of-service (DoS) attack on your network equipment or service.
This technique has been around for a long time, but even today it is not uncommon to find a router susceptible to this kind of attack on a LAN.
Lastly, a Christmas Tree Packet can also be sent over the Internet, most of the times from a spoofed source address, but in this case it is called a Martian Packet.
So stay aware, monitor and configure your network correctly, run tests, and enjoy the holiday season :)
